Ransomware has moved out of the realm of the anecdotal to the endemic. Two out of three organizations have reported a ransomware attack in 2021, with attacks almost doubling from the year before. The average ransom paid by organizations that were victims of “successful” ransomware attacks, where their data was encrypted, has increased nearly fivefold to$812,360. While that is a hefty amount in itself, the insidious nature of ransomware leads to far-reaching repercussions – an expense that keeps growing. Understanding the true cost of ransomware is key to effectively mitigating the risk and combating it with prevention and recovery mechanisms. Let’s examine and sum total the far-reaching impact of a ransomware attack on your business.
The True Cost of a Ransomware Attack. Circa 2022
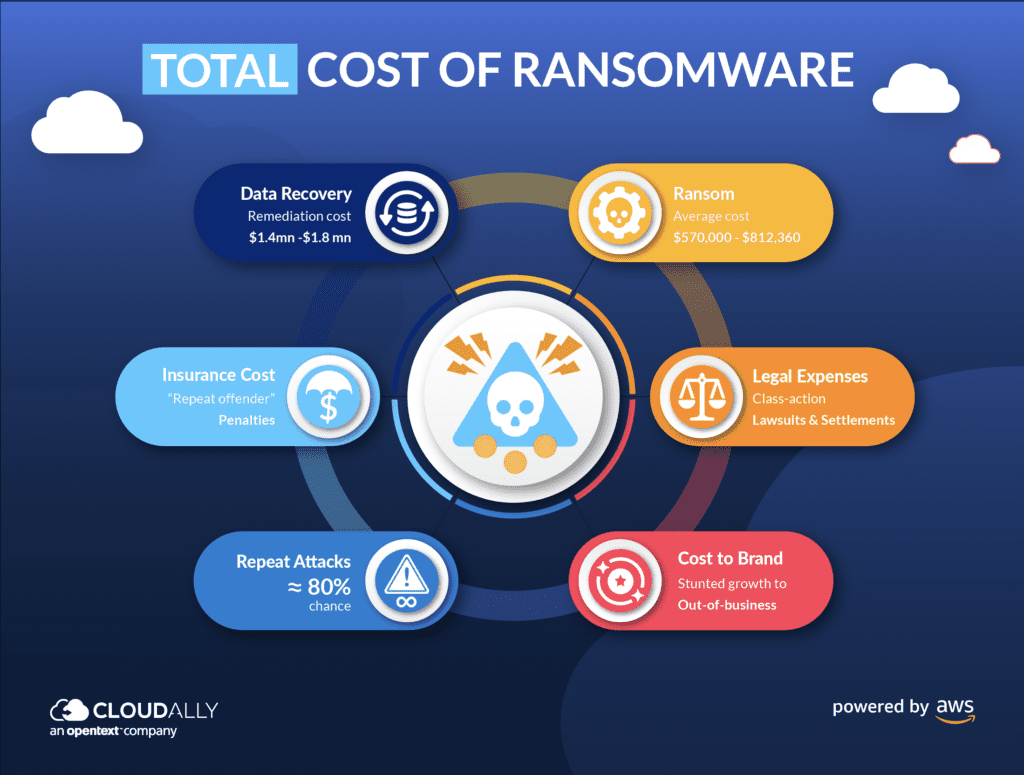
When it comes to ransomware, the cost isn’t just financial. In fact, the true cost of a ransomware attack can be widespread; impacting everything from a company’s reputation to its bottom line. Here’s a look at the various cost associated with a ransomware attack:
The Ransom
Ransomware can cost a company millions of dollars in losses, both in terms of the ransom itself and in terms of lost productivity and revenue. Let’s start by examining the big “R” – its trends and average.
- Ransoms are rising: The State of Ransomware 2022 Report details that in 2021, 11% of businesses paid ransoms of $1 million or more, up from 4% in 2020. And the hackers aren’t letting you get off the hook for cheap either; the proportion of those paying less than $10,000 decreased to 21% from 34%.
- Average Cost of Ransom: Two recent studies by Sophos and Pao Alto peg the average cost of ransomware between $570,000 – $812,360
- FYI, It’s Illegal to Pay: The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) announced in 2020, that paying ransom to cybercriminals in most cases is illegal.
Ransom paid, now get on with business? Not quite.
Legal Expenses
If sensitive data is encrypted and held for ransom, it could result in costly legal action from customers or regulators. A consistent level of service is often included in service level agreements (SLAs). SaaS data loss or a data breach may result in delayed or diminished customer support, which can result in legal fines.
- Class-action lawsuits and settlements: The Washington Post succinctly puts it “First came the ransomware attacks, now come the lawsuits”. From hospital system Scripps Health to retail giant Target to gas company Colonial Pipeline to Carnival Cruises – no industry is spared a class-action lawsuit by aggrieved customers. Most cases end up being settled out-of-court, as companies opt to pay off hacking victims instead of fighting expensive and long-drawn court battles.
- Secure PHI, PCI, and PII data: Regulatory and legal fines can be especially high for personal health information (PHI related to HIPAA), financial data and Payment Card Industry (PCI), and Personally Identifiable Information (PII).
- Evolving Lawsuits: Customers are not just seeking damages due to lost data, but also due to the increased risk of identity theft or credit card fraud. Owing to the increase in supply chain attacks, downstream firms can also sue for loss in business continuity, incident response costs, and recovery expenses resulting from the ransomware attack.
Cost to Reputation/Brand/Business
A ransomware attack can damage a company’s reputation, leading to lost customers and business opportunities. Your customers and vendors are risk-averse; and will consequently be wary of engaging with a company post a ransomware attack. Your ability to bounce back with quick disaster recovery and seamless business continuity will be critical to deciding the fate of your brand’s reputation.
- Stunted Growth: A ransomware attack can damage a company’s brand and reputation, making it difficult to attract new customers and business partners. SaaS data loss or a breach can stifle growth in its tracks. Consider that access to your central SaaS platform – Salesforce or Microsoft 365 – is lost. How are you going to generate new sales or expand your client base if access to your Salesforce/M365 email, documents, calendar, contacts, etc. has been destroyed or corrupted? When Sales is fighting fires calming customers impacted by the ransomware attack, how can they generate new ones?
- Out of Business: Research from the National Cyber Security Alliance indicates that 60 percent of SMBs (Small and Medium Businesses) go out of business within six months of falling victim to a data breach or cyber attack. 90 percent of companies said the assault had affected their ability to function, and 86% of private-sector victims claimed they had lost business and/or revenue as a result of the attack.
Remediation & Recovery Post-Attack
Ransomware can result in significant downtime for a company, costing it money and productivity. While most IT organizations are aiming for a 2:1 ratio, disaster recovery experts say that the typical productivity loss is 8 to 20 percent during an outage. During the loss of connectivity, critical daily functions like developing the business, releasing new items, and customer care may be affected. It can even impact your ability to release a new product feature, release, or bug fix.
- Increasing downtime costs: Downtime is expensive. Sophos reports that the most recent ransomware attack in 2021 cost an estimated $1.4 million to recover from. It took on average one month to repair and restore operations back to normal. Calculate the cost that downtime can rack up for your organization with our Downtime Calculator
- Post-attack remediation: In 2019, the average cost of cleaning up after a ransomware assault for a firm that had been attacked was $761,000. That amount, as per various reports, has risen to $1.4 million to $1.85 million in 2020.
- Ransom paid, but data lost: Forbes reported that even after paying the ransom, only 65% of data was restored. So do not expect that data and business continuity will be restored after paying the ransom (unless you have a reliable backup to recover your data from).
Cascading Costs
A ransomware attack is like a gift that keeps giving.
Higher Insurance Premiums: Many businesses rely on cyber insurance to help them recover from a ransomware attack, and most cyber insurance does pay out. The cyber insurance industry has smartened up to the increasing frequency of malware attacks and now demand stringent cybersecurity measures to be put in place with more complex or expensive policies. Similarly, insurance companies extend similar penalties for “repeat offenders” – higher premiums, bigger deductibles, and the like.
Repeat Attacks: Once hit, you are on their radar; or rather, they are in your network. Backdoors, stolen passwords, and other similar methods are used that allow continued access for the hackers into your system. If organizations don’t clean up their data or fix the underlying issues, they’ll have a lot of potentially hazardous material and vulnerabilities, thus risking another attack. A recent report states that of the 28% of respondents who paid the ransom, 80% of them got hit with a second ransomware attack, and 68% percent got hit a second time within a month and for a higher ransom.
Whew!
Mitigating the Cost of a Ransomware Attack
While we’re reeling under the cost of ransomware, let’s also examine ways we can use to mitigate the risks and cost of a ransomware attack.
- Develop a Robust Incident Response Plan: Ransomware will find its way to infiltrate your cybersecurity armor. Prepare a solid ransomware incident response plan with detailed steps for both the short-term and long-term response. Your plan will generally encompass 5 steps to assess, mitigate, respond, communicate, and restrospect.
- Backup is Your Best Bet: Security experts worldwide including the CISA recommend that “Backing up Is your best bet against ransomware”. Backups are the most effective method to ransomware-proof your data, but they must also be cyber-resilient, which means that they must be able to withstand ransomware attacks and hold an uninfected and accurate copy of your data to restore from. Check out these 4 backup best practices for ransomware recovery to ensure that your backups are a reliable safety net in the event of a ransomware attack.
- Don’t Skimp on Cyber-insurance: General liability insurance will typically protect an enterprise against some or all costs of lawsuits including attorney fees and settlements. However, go over your policy carefully. As mentioned above, given the rise in attacks, insurance carriers have reevaluated their coverage options.
- Constantly Improvise your Defenses: Reevaluate your endpoint protection, firewalls, and identity security constantly and tweak them based on the latest malware and ransomware techniques. For instance, as more ransomware attacks now also involve extortion, layer your cybersecurity protection.
Ransomware Recovery with CloudAlly
CloudAlly Backup provides encrypted and immutable cloud backups for Microsoft 365, Google Workspace, Salesforce, Dropbox, and Box. It includes unlimited backup on secure Amazon S3 storage with easy recovery from any point-in-time. CloudAlly also offers data backup with S3 Object Lock for sensitive data which retains records in a non-rewritable and non-erasable format to meet stringent data regulations. Our solutions implement application security best practices, such as multi-factor authentication (MFA), Two Factor Authentication (2FA), Okta integration, OAuth permissioning, robust password protection, password and access key rotation, and vulnerability and patch management.
Mitigate the cost of ransomware with reliable recovery from any point in time. Book a 1-1 demo or start a free trial now!


