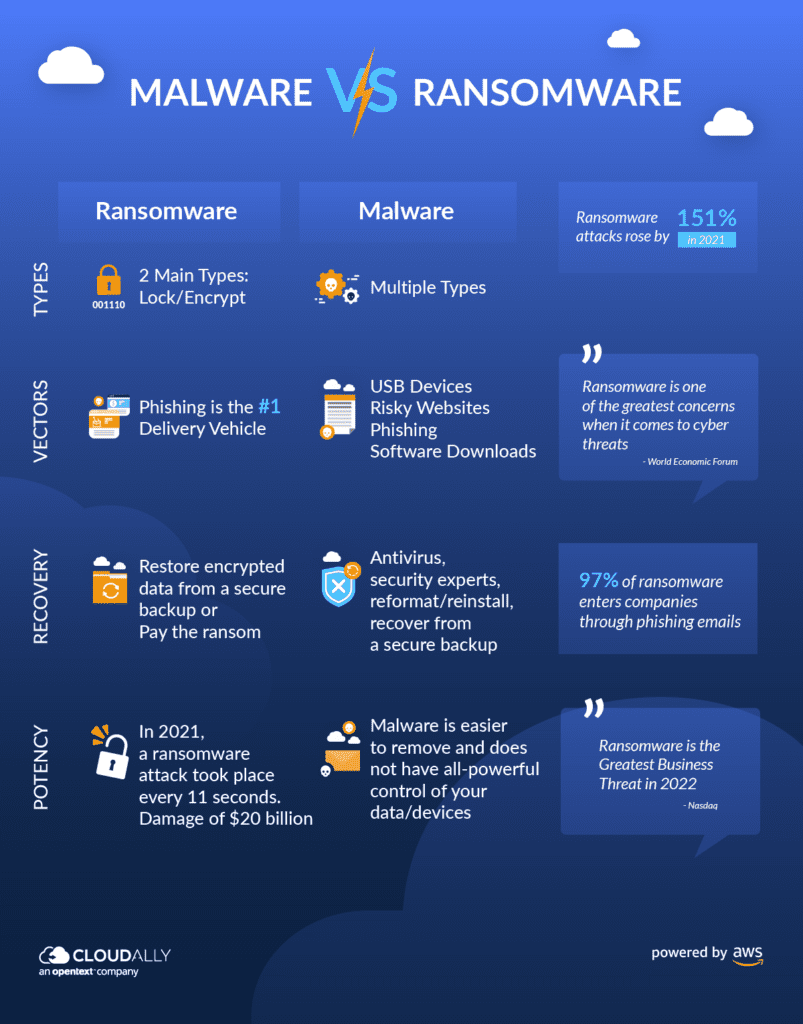
Both malware and ransomware strike terror and dread in the heart of any organization. Data protection trends for 2022 predict that smart ransomware and malware infused with AI and ML will be the number one Cybersecurity threat for organizations. The World Economic Forum’s annual Global Risks Report 2022 cautions that ransomware attacks rose by 151% in 2021 and that “ransomware is one of their greatest concerns when it comes to cyber threats”. Let’s do a deep dive into the malware vs ransomware dilemma, examine the difference between them and provide proven, practical pointers to secure your organization against these malicious software programs.
Malware Vs Ransomware – What’s the Difference Between Them?
A concise infographic with a deep-dive below:
What is Malware?
Malware is short for “malicious software” and refers to all forms of hostile or harmful software that can affect a device or system including ransomware malware. In general, malware is a computer program that enters a device without the owner’s knowledge and permission. In some cases, malware can be transferred from one computer to another as part of a virus. There are many types of malware infections including viruses, spyware, trojans, worms, and ransomware.
Types of Malware
There are seven major types of malware, although malware can fall into more than one category. They are:
1. Computer Virus
A computer virus is a type of malware that, when executed, replicates itself in order to spread to other devices.
2. Worm
A worm is malware that spreads by replicating itself over and over without human interaction.
3. Trojan Horse
A Trojan Horse malware allows the creator access to the device it was installed on by intercepting communication between two computers or making it appear that communication was made while actually sending data back to the creator instead.
4. Backdoor Attacker
A backdoor attack occurs when malware gains access to a system through an existing piece of malware already on the device.
5. Rootkit
A rootkit malware program acts like a fake driver to ensure that malware runs on an operating system while also taking ownership of device files and functions, making it hard for malware removal programs to find or delete it.
6. Ransomware
Ransomware is also a type of malware. It encrypts data, such as files and folders on a computer or server, and locks it until the malware creator receives payment in cryptocurrency like Bitcoin.
7. Scareware
Scareware is a type of malware that uses fear to deceive people to install malware or ransomware. Most often, scareware is delivered through a pop-up ad and relies on social engineering to deceive users into believing they need fraudulent anti-virus software. The objective of scareware varies greatly: from selling nonsense phony tools in order to install damaging malware that exposes private information to installing ransomware, which holds the user’s data hostage in exchange for money.
What is Ransomware?
Ransomware malware is malware that encrypts data, such as files and folders on a computer or server, and either blocks access or encrypts it until the malware creator receives payment in cryptocurrency like Bitcoin. Ransomware has become one of the most common types of malware because it specifically targets devices with the goal to encrypt data on those devices until users pay ransom in cryptocurrency like Bitcoin. Ransomware has grown into the most prominent malware threat. Experts estimate that one attack took place every 11 seconds in 2021 resulting in total damage costs of US$20 billion.
Types of Ransomware
Here are the main types of ransomware that all target data and devices differently.
1. Locker Ransomware
This type of ransomware locks the device’s screen, preventing access to any of its data or functions. To unlock it, users must pay ransom in cryptocurrency like Bitcoin.
2. Cryptolocker/Encryption Ransomware
The malware creator encrypts files on the infected device and demands payment for a key code to decrypt them again. However, it does not block basic computer functions. This adds to its potency as users can see their files but cannot access them and are faced with the threat – “If you don’t pay the ransom by XX-XX-XXXX, all your files will be deleted”. When Cryptolocker malware encrypts data, it cannot be decrypted without a unique key that is only available to malware creators. This malware uses asymmetric encryption where two keys are generated: one public which can decrypt an encrypted file and another private that unlocks the malware’s network location from where files can be bought back online. Users have to pay a ransom in cryptocurrency to get the key to decrypt their data.
3. RaaS (Ransomware as a Service)
This recently evolved type of ransomware demonstrates how “mainstream” ransomware has become. It refers to malware hosted anonymously by a “professional” hacker that handles all aspects of the attack, from distributing ransomware to collecting payments and restoring access, in return for a cut of the ransom.
Malware Vs Ransomware – Difference Between Ransomware and Malware
Malware Vs Ransomware: A Quick Snapshot
Parameter |
Ransomware |
Malware |
|---|---|---|
Vector |
Few Vectors: Ransomware has a limited range of distribution methods: the most frequent method by far is phishing emails, though file sharing and unsafe websites are also used to distribute ransomware. | Multiple Vectors: In comparison, Malware is transmitted in a variety of ways: USB devices, risky websites, phishing emails, malicious links, and software downloads are just a few of the most prevalent methods. |
Type |
Two main types: Locker ransomware and crypto-ransomware are the most frequent types of Ransomware. | Types increasing by the day: Malware refers to any sort of harmful computer software, including viruses, worms, spambots, spyware, adware, Trojan horses, and ransomware. |
Recovery |
Difficult: Victims are generally forced to either restore their encrypted data from a secure backup or pay the ransom. | Easy: Malware is often easier to get rid of than ransomware. Antivirus programs can be used to detect and delete a variety of malware. Complex malware may require the help of a security expert. For complete malware removal – formatting drives, reinstalling applications, and full data recovery from a secure backup are recommended. |
Potency |
Lethal: Ransomware wins, hands down! It can cause considerably more damage than most types of malware. | Dangerous: The majority of harmful side effects from malware include decreased system performance and a threat actor having control over computing resources and data. Because malware is easier to remove and does not do as much harm, its consequences are often minor. |
Malware Vs Ransomware – 5 Cybersecurity Best Practices to Combat Both
There are a variety of ways to protect devices from ransomware and malware, but some methods are more effective than others.
#1 Put Basic Checkpoints in Place: Malware Prevention and Detection Software
Security software such as malware removal tools, anti-virus software, and firewalls can help to detect and remove malware before it has a chance to do any damage. They can also help protect devices from ransomware by blocking the malicious code from being installed in the first place.
#2 Don’t Skimp the Backup: The Only Way to Quick Recovery
One of the best ways to protect against ransomware and malware is to have a cloud-based data backup and recovery plan in place. This type of plan will allow users to back up their data to a secure location outside of their network, making it difficult for ransomware and malware to reach it.
If ransomware or malware does manage to infect a device, the backup can be used to restore the data to its previous state. This will help ensure that the organization does not lose any important files or data as a result of the attack.
#3 Hone the Weakest Link: Train Cyber-secure Employees
Cybersecurity training for employees is essential for protecting an organization from ransomware and malware attacks. Employees need to be aware of the dangers of opening emails or clicking links from unknown sources, as these are often how ransomware and malware are spread.
Additionally, employees should be taught how to recognize malicious code, and how to properly report any incidents. Employees should also be taught how to protect their devices from ransomware and malware attacks. It is important for employees to receive such training in a regular, informal, and interesting way such as lunch and learns, incentivized quizzes, contests, etc.
#4 Restrict Employee Access: Strictly Need-to-Know
One way to help protect an organization from ransomware and malware is to restrict employee access to sensitive data. This can be done by implementing a number of security measures, such as user authentication, firewalls, and malware protection. User authentication will help ensure that only authorized users have access to sensitive data. Firewalls will help to block unauthorized access to the network, while malware protection will help to detect and remove any malware that may be present on the device.
Restricting employee access to sensitive data can also help to minimize the risk of a ransomware or malware attack. By limiting the number of employees who have access to critical files and data, the organization can reduce the chances that an attacker will be able to successfully launch an attack.”
#5 Create a Thorough Incident Response Plan: You’re Attacked, What Next?
An incident response plan is a document that outlines the steps that should be taken in the event of a ransomware or malware attack. It typically is a part of the Business Continuity and Disaster Recovery Plan (BC/DR), a must for a cybersecure organization. The purpose of an incident response plan is to help organizations respond quickly and effectively to a ransomware or malware attack. By having a plan in place, organizations can minimize the damage that the attack may cause and prevent it from disrupting normal business operations.
An incident response plan should include information on the following:
- The steps that should be taken immediately following a ransomware or malware attack, including notifying the appropriate people and isolating the infected device.
- How to investigate the source of the attack and how to contain it
- How to recover and restore data that has been encrypted or damaged by the ransomware or malware
- How to prevent future attacks from happening
An incident response plan should be reviewed and updated on a regular basis to ensure that it is up-to-date and effective.
Read this detailed guide to protect your Microsoft 365 data from a malware attack.
Malware Vs Ransomware – Recover From Both With CloudAlly
Backup is the only surefire way to restore business-critical data seamlessly and rapidly. The US Government’s Cybersecurity and Infrastructure Security Agency (CISA) recommends backup to quickly restore a non-encrypted version of data, thus recovering quickly from ransomware and reducing its damages. More specifically, it recommends backup on the cloud rather than backup on-premises. This is because the backup storage is abstracted from the infrastructure being attacked.
“Backups are critical in ransomware recovery and response; if you are infected, a backup may be the best way to recover your critical data.”
– Cybersecurity and Infrastructure Security Agency (CISA)
Recover your Microsoft 365, Google Workspace, Salesforce, Box, and Dropbox data ASAP with CloudAlly Backup when struck either with malware and/or ransomware.
Start a full-feature 14-day trial now – Zero setup, No Payment details