5 Strategies for Small Businesses to Mitigate, Respond, and Recover from Ransomware
As a small or medium-sized business owner, you should be concerned. Hackers are shifting their focus from big-sized enterprises to SMBs as a lucrative target for ransomware attacks. 82% of ransomware attacks in 2021 targeted small and mid-sized businesses. How can SMBs with limited cybersecurity resources and ransomware recovery expertise overcome an attack? Read on for five practical strategies that your SMB can use for ransomware protection to mitigate, respond, and recover from ransomware attacks.
What is Ransomware?
Ransomware is a type of malware that encrypts files on a computer or server and demands a ransom payment to unlock them. If users want to regain control of their device, they must pay a ransom in cryptocurrency such as Bitcoin. While phishing is the main vector for ransomware, it can also be delivered through security holes and infect a system passively, without any user input or action.
Ransomware has been around since the late 1980s, but it wasn’t until recently that it became a major threat to businesses and individuals. It is the most popular type of malware with an estimated attack taking place every 11 seconds in 2021. Ransomware is so ubiquitous that it can be “outsourced” with RaaS (Ransomware as a Service) options. The potency of ransomware has evolved with ransom demands not only to decrypt files but also to avoid going public with sensitive data that has been exfiltrated.
Why are SMBs Being Targeted by Ransomware Attacks?
“You can hit the jackpot once, but provoke such a geopolitical conflict and you will be quickly found. It is better to quietly receive stable small sums from mid-sized companies.”
– LockBit 2.0 Ransomware Gang Member
So, what makes SMBs such an attractive target for ransomware attackers?
- Sub-par cybersecurity: SMBs usually have less robust security than large enterprises. This makes them an easier target for hackers to breach. In a survey of more than 1,400 MSPs, 89% reported that while SMBs should be very concerned about the threat of ransomware, only 28% of MSPs have cybersecurity best practices in place.
- More likely to pay the ransom: SMBs often don’t have the same resources as larger enterprises for ransomware recovery. This makes them more likely to pay a ransom demand.
- Less risky for the hackers: Coveware reports a “tactical shift” by ransomware groups pressured by tough law enforcement takedowns, seizures, arrests, and extraditions in Q3 2021. Fearing legal repercussions, ransomware groups have refined tactics “to extort companies that are large enough to pay a ‘big game’ ransom amount but small enough to keep attack operating costs and resulting media and Law Enforcement attention low.”
The bottomline? As an SMB it’s best to prepare for the eventuality of ransomware and put into place methods to blunt the attack. Let’s take a look at five strategies that can be used to mitigate, respond, and recover from ransomware attacks.
How to Protect Your SMB From Ransomware Attacks? 5 Strategies
Owing to the increase in ransomware attacks on small and medium-sized businesses, the Institute for Security and Technology’s Ransomware Task Force formulated a “Blueprint for Ransomware Defense”. This report written in plain speak sought to remove the barriers for SMEs with limited cybersecurity resources and expertise in defending against ransomware. We examine the recommendations in the report which are mapped to the National Institute of Standards and Technology (NIST)’s cybersecurity plan.
1. Identify: SMB Ransomware Protection
Understand and identify the business impact of cybersecurity across infrastructure, network, employees, and data.
Although it can be difficult to keep track of all these safeguards, they are essential for dutiful defense and post-ransomware response:
- Establish and maintain a detailed Enterprise Asset Inventory and Software Inventory
- Document the Data Management process and the Supply Chain Risk Management Strategy
- Track the Inventory of Accounts
2. Protect: SMB Ransomware Protection
In order to secure your infrastructure and data, you need to put certain safeguards and frameworks in place. Analysis suggests that practicing proper cyber hygiene can defend against over 70% of ransomware attack techniques. This will help mitigate some of the risks.
- Secure your network configurations and manage a robust firewall,
- Restrict access on a strict need to view/access level. Regulate access to sensitive data and systems by using least privilege principles.
- Implement mandatory MFA/2FA. Use strong passwords and enable two-factor authentication whenever possible.
- Only support a set list of OS. Make sure all devices are running the latest version of their operating system.
- Training your employees on cybersecurity best practices is essential to protecting your business from ransomware attacks. In order to protect your company from cybersecurity threats, employees should be trained to spot suspicious activity and know what to do if they think their account has been compromised. You should also have a plan in place for how to communicate during a ransomware attack.
- Manage vulnerabilities with patch and update management
- Back up your data regularly so you can restore it if it’s encrypted by ransomware.
- Have your malware defenses in place such as monitoring tools, ransomware canaries, DNS filtering, and anti-malware software updates.
3. Detect and Respond: SMB Ransomware Protection
Early detection is key to responding to a ransomware attack quickly and minimizing the damage. There are a few things you can do to enable detection:
- Implement activity monitoring to look for suspicious activity on your network. Use file integrity monitoring to look for changes in critical files.
- Develop a detailed Ransomware Incident Response Plan
- Collect and record audit logs
4. Recover: SMB Ransomware Protection
Even if an SMB pays the ransom, research from Webroot has found that approximately 17% of those companies don’t get their data back. Here are some activities to keep data secure, recover quickly after a disaster, and maintain business operations after a cybersecurity incident.
- Put the Ransomware Incident Response Plan in place.
- Recover your data from an uninfected backup.
5. Improvise: SMB Ransomware Protection
Even the best plans get outdated – keep your plans relevant by regularly reviewing and improving them. By doing this, you will be able to find areas of improvement in your plan before an actual attack occurs.
- Review and improve existing plans and policies namely the DRP or the BCDR plan.
- Regularly check your backup and recovery plan, so you can be sure of a successful restore when you need one (here are pointers for backup and recovery testing)
For tailored recommendations on Microsoft ransomware protection, read this blog on Microsoft 365 ransomware protection.
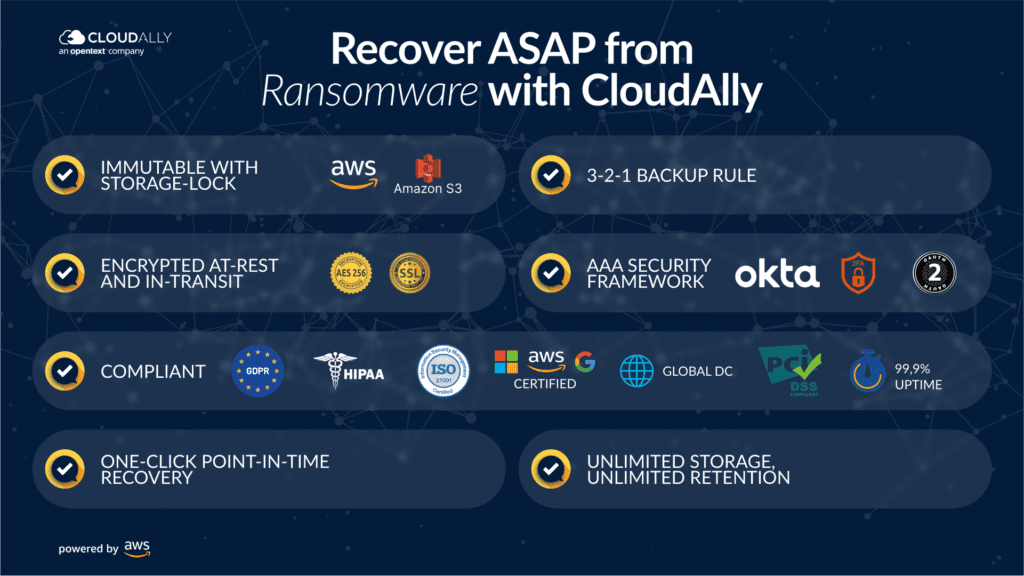
Recover from Ransomware ASAP With CloudAlly Backup – Tailored for SMBs (Small and Mid-sized Businesses)
CloudAlly’s SaaS Data Protection platform secures all your SaaS data – Microsoft 365, Google Workspace, Salesforce, Dropbox, and Box. Ideal for SMBs looking for a single solution for multi-platform backup. Backups are stored on stringently secure AWS S3 backup (with unlimited storage and retention). When ransomware strikes, simply recover with a few clicks. Watch How!