Secure SaaS Backup
Compliant, Secure and Audit-Ready
Your valuable SaaS data is only as secure as its backup. Which is why it is critical to ensure that your backup solution is dependably secure.
Security has been in our DNA right from when we pioneered SaaS backup a decade ago. We’re fanatical about security for all our backup solutions for Microsoft 365 (Office 365), G Suite, Salesforce, Dropbox, and Box. We have internationally recognized accreditation, stringent application security, and rigorous data protection. We continue to strive beyond the required compliance standards to achieve best-in-class security.
Is Your SaaS Backup Secure?
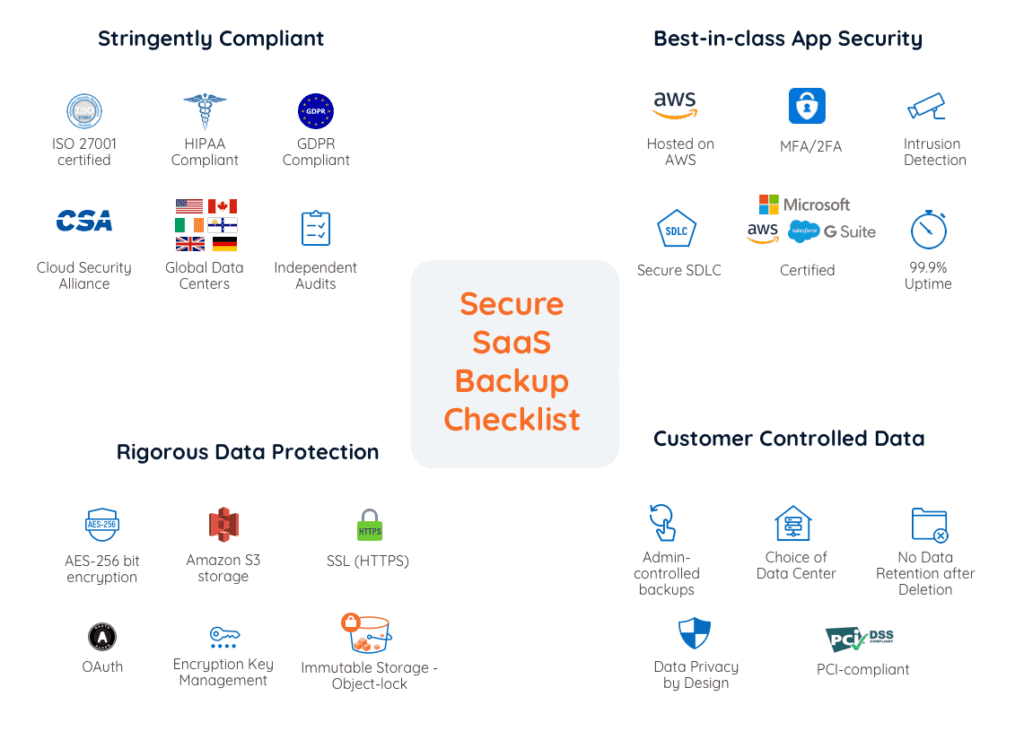
Stringently Compliant

ISO 27001 and HIPAA Compliant
CloudAlly is ISO 27001 certified which is an internationally recognized accreditation for information security management. We are also HIPAA compliant and can provide a BAA Agreement on request.

Cloud Security Alliance (CSA)
CloudAlly participates in the Cloud Security Alliance STAR (Security, Trust and Assurance Registry) program using CSA’s Cloud Controls Matrix (CCM). CCM is a framework of cloud-specific security controls ensuring that participating organisations adhere to leading industry standards, best practices and regulations.

CloudAlly is based in Israel, which was approved by the European Commission as a country providing “adequate protection” for personal data. We’re committed to ensuring that our services are fully compliant with GDPR. To read more about our GDPR compliance Click Here

Data Centers in NA, EU, U.K. or APAC
Adhere to local regulatory requirements with your choice of data centers spread across Canada, Germany, Ireland, Sydney, U.S., and the U.K. Or backup to your own storage with Bring Your Own Storage support (BYOS)
Best-in-class Application Security

Reliable Amazon Hosting
CloudAlly is hosted on Amazon Web Services (AWS), which means that we’ve built CloudAlly on a foundation of reliable security right from the beginning.

Secure MFA/2FA Authentication and Okta Integration
Our solutions implement application security best practices, such as multi-factor authentication (MFA), Two Factor Authentication (2FA), robust password protection, password and access key rotation, and vulnerability and patch management. We also support Okta integration.

Intrusion Detection
Virtual private cloud, identity and access management, stateful and stateless firewalls, application-level firewalls, and intrusion detection further strengthen the security of our solutions.

Certified by Google, GoDaddy, and others...
Our websites have Secure Security Authorization (HTTPS) SSL Certificates issued by GoDaddy. We’re certified by solution providers such as Google Workspace formerly known as G Suite, and others.
Rigorous Data Protection

Data Encryption in-transit and at rest
All data is stored in Amazon S3 storage and encrypted using advanced AES-256 bit encryption algorithms. Transmitted data is encrypted and secured using SSL (HTTPS) enabled servers.
Our servers are strongly secured, hardened and include the latest security patches. All end-user sessions and interactions with the CloudAlly backup solution use SSL/HTTPS.

Encryption Key Management
CloudAlly uses a unique encryption key for each customer, and the keys are securely stored. Use of a unique S3 folder for each customer ensures data isolation. Additionally, every backup task has its own initial vector, which is stored securely and separately from the user key. This technique helps CloudAlly to encapsulate the users’ data. Immutable Storage – our Object-Lock capability further minimizes the possibility of accidental or malicious loss of data.

OAuth Permissioning
CloudAlly uses industry standard OAuth for permission based access when possible, eliminating the need to enter or store user credentials on the CloudAlly system. The OAuth “token” limits access to exactly what CloudAlly needs to do and doesn’t provide general access to your account. You can revoke authorization at any time. If OAuth is not available for a specific service then credentials are stored using advanced
AES-256 bit encryption algorithms.
Customer has Full Control of Data

Admin-controlled backups
Customer backup data is not accessible directly, it can only be accessed using the CloudAlly platform. CloudAlly backups can only be activated, deactivated or restored by the customer’s Data Administrator.
Internal CloudAlly staff do not have access to customer data, and only a limited number of core team members have access to production keys based on a “need to know” policy for problem resolution, and all access is logged in the audit log.

No Data Retention after Deletion
All backup data is retained as long as you maintain your CloudAlly subscription. If you choose to cancel your subscription, your data will be deleted from the CloudAlly archives within 5 Days. If you deactivate an individual user backup or database table/domain, that data will be deleted within 24 hours so we recommend downloading the data prior to deactivation if you want to retain the backed up data for local archiving.

Data Privacy by Design
CloudAlly archives can optionally be stored in Amazon data centers in Canada, Germany, Ireland, Sydney, U.S., and the U.K as needed for compliance with data privacy directives. Or Bring Your Own Storage (BYOS)

Payment Processing
Payment processing, including credit card information, is hosted by our payment processor which is fully PCI compliant. No payment information is handled or stored on the CloudAlly system.
Security Built into Our Product DNA
For a product to be robustly secure security has to be built into the SDLC (Software Development Lifecycle). Security has to form the bedrock of company culture and credentials have to be independently evaluated.
CloudAlly’s Secure SDLC
Our Culture of Security
In the design phase — CloudAlly’s security team reviews all product design and requirement documents to identify any risks early in the development process.
CloudAlly maintains a comprehensive employee on-boarding process, including a device management solution to all laptops, encrypting hard disks, enabling firewalls, and implementing a VPN.
In the development phase — We integrate security tools into the process that run whenever code is committed to detect any vulnerabilities.
All new hires are subject to a pre-employment background check in order to verify identity, references, and criminal history.
In the testing/release phase — We perform penetration testing on our product and test extensively to detect potential vulnerabilities prior to deployment.
We require all new employees to complete a comprehensive security awareness training, and we conduct annual training to maintain continued awareness.
CloudAlly's Validated Secure Credentials
CloudAlly conducts periodical penetration tests, in order to identify vulnerabilities in our web application/s with other integrations. We collaborate with an Independent Security Evaluator (ISE) to perform network, cloud, and application penetration testing and vulnerability testing.
CloudAlly stands fast in its commitment to seeking out the latest and most innovative ways to stay ahead of potential threats to your data. This is our method of promising our customers that we’re always vigilant so that you can feel safe entrusting us with your business critical data. We know that’s what the market has come to expect from us, and that’s why we hold ourselves to the highest security standards possible.

Compliant
Web Service (AWS)

Compliant
Strong
Encryption
Global
Datacenters
Intrusion
Detection
Compartmentalized
Access



7 Reasons Why Enterprises Need SaaS Backup And Pointers to Maximize Its ROI.
In our eBook you will find 7 Reasons Why Enterprises Need to Secure SaaS Backup And Pointers to Maximize Its ROI.
Learn About:
- Reasons to Backing up
- Pointers to Save on Backup
- … & much more.