- Home
- Remote Workforce Security
Guaranteed Remote Productivity using Cloud Backup
How to Secure your Remote Workforce?
Practical pointers to secure your remote workforce and
protect business-critical SaaS data
Three Essential Guidelines for Improved Disaster Recovery & Business Continuity, in the Work-From-Home Era
How CloudAlly can help:
CloudAlly pioneered SaaS Backup for the enterprise in 2011. Our backup solutions for Microsoft 365, G Suite, Salesforce, Dropbox, and Box are tried and tested by organizations with thousands of users.
We’re top-rated by Gartner Capterra and G2, and were voted as a leading SaaS backup solution in a Newsweek survey by 10,000+ IT Pros . We’re secure, scalable, and tailored to support the remote workforce.

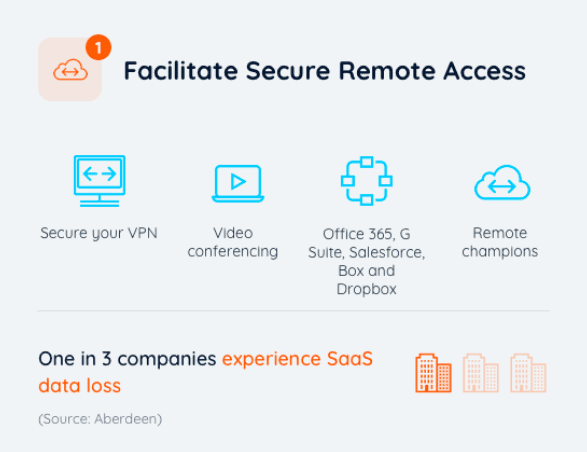
Comprehensive Cloud-to-Cloud Backup: Complete SaaS data protection of Microsoft 365 – Mail, Calendar, Contacts and Tasks, OneDrive, SharePoint, Groups and Teams (heavily used by remote teams). G Suite -Gmail, Team Drives, Sites, Calendars, Contacts, Tasks, and Metadata backup. Salesforce data, metadata, Chatter feeds, and Metadata. Box and Dropbox backup.

SaaS Backup on Amazon AWS Storage: CloudAlly stores backups on the stringently secure Amazon AWS S3 storage and encrypted using advanced AES-256 bit encryption Backup solutions with on-premises storage cannot provide remote data security, with the same ease and control that SaaS backup can.

Easy Remote Workforce Management: Simplified employee on-boarding and offboarding with bulk activation, automated addition/deletion users, and backup of inactive accounts.

OOTB Setup, Zero Adoption Effort: Seamless integration with all SaaS platforms – Microsoft 365, G Suite, Salesforce, Box and Dropbox, intuitive UI with admin-friendly tools.

Flexible Remote Recovery Options to any Storage with Unlimited Retention: Self-service, point-in-time, granular, and cross-user restore. Non-destructive with unlimited retention. Backup to your own cloud storage.

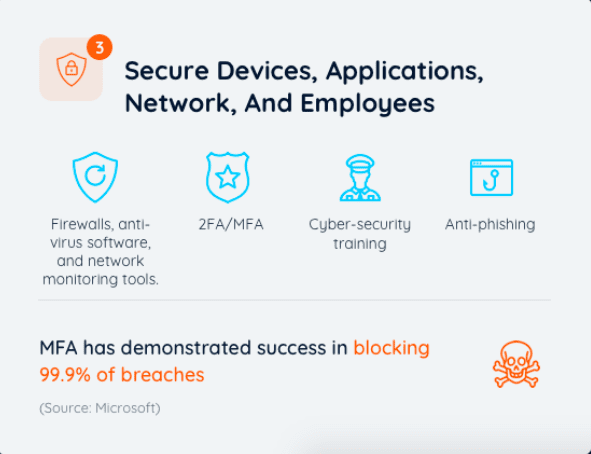
Secure and Audit-Ready: Global data centers, GDPR, HIPAA and SoX compliant, ISO 27001 certified, MFA/2FA, OAuth and OKTA support, AES-256 data encryption, 99.9% uptime SLA.

High ROI with Unbeatable Pricing: Custom discounts for bundles, high-volume and multi-year packages. Save on platform license costs with inactive account backup.

Tier 1 – 365x24x7 Real-person Customer Support: Highly-responsive customer service with a multi-channel Customer Support Hub. We’re always on-call to resolve your data protection challenges.
How do you Secure the Remote Worker?


Free Ebook
Practical pointers to optimize Disaster Recovery with a remote workforce
✖
Download eBook

Consult with our Security experts
Got Questions? Why not talk to our backup consultant, to learn more about how to enable a recovery from any point in time. No obligation.
Schedule a 1-on-1 Consultation
with our backup expert