- Home
- Ransomware Data Recovery
Microsoft Office 365
Ransomware Recovery
Recover your Microsoft SaaS data in Minutes with CloudAlly

Ransomware Data Recovery
"Ransomware is the greatest business threat in 2022"
NASDAQ
"Backups are critical in ransomware recovery and response; if you are infected, a backup may be the best way to recover your critical data."
CISA (Cybersecurity and Infrastructure Security Agency)
Quick data recovery and reduced downtime are critical to mitigate the risk and the cost of ransomware. Get your data back ASAP with CloudAlly Backup
- Secure, unlimited, encrypted Amazon S3 SaaS Backup on the cloud
- Immutable backups that can’t be compromised
- Quick recovery with seamless point-in-time or granular restore
- One solution to secure all your SaaS data
Recover from Ransomware with CloudAlly
Watch How!
Book a Demo
Schedule a 1-1 Meeting with
Avik, our Backup Expert

Ransomware Recovery in Action
Watch How!
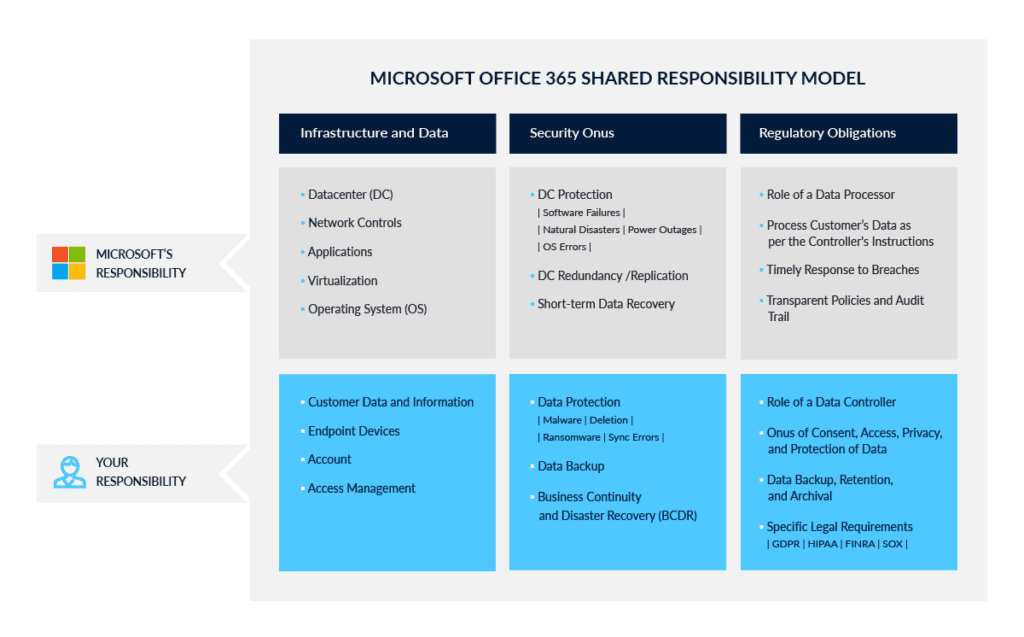
Does Microsoft 365 Protect You from Ransomware?
Microsoft's Shared Responsibility Model Puts the Onus On You
“Microsoft cloud services are built on a foundation of trust and security. Microsoft provides you security controls and capabilities to help you protect your data and applications. You own your data and identities and the responsibility for protecting them, the security of your on-premises resources, and the security of cloud components you control."
Microsoft